When you select Protect a virtual machine, the Select virtual machine page will appear.
|
|
Note: |
While generic SCSI device mappings in virtual machines are supported by Double-Take Availability for VMware Infrastructure, the generic SCSI device will not be created on the target virtual machine. This is necessary because the target virtual machine will fail to start if the SCSI device hardware does not exist on the target ESX host. Upon failback, the generic SCSI device will be mapped back to the original source. If a source virtual machine with a generic SCSI device mapping is replicated to target and the entire protection job is removed, then re-created in the reverse direction, the SCSI device will not be mapped back to the original source. |
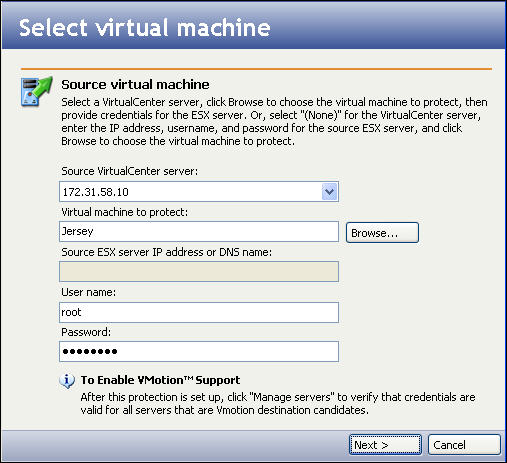
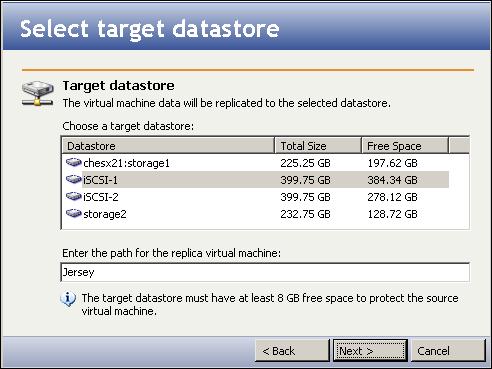
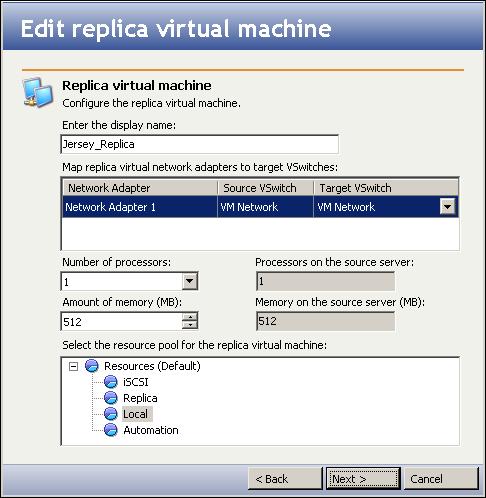
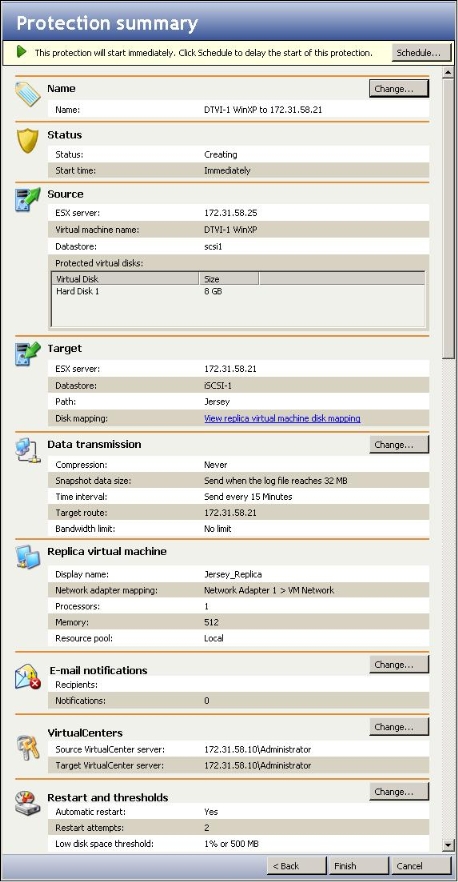
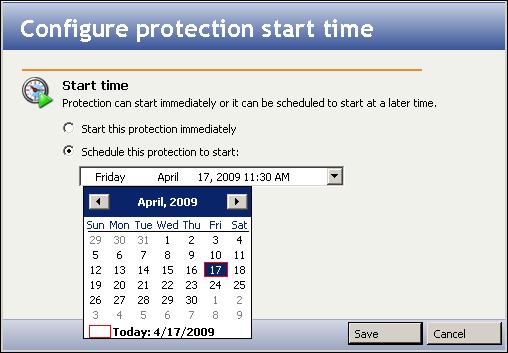
Enter the following information for the source server:
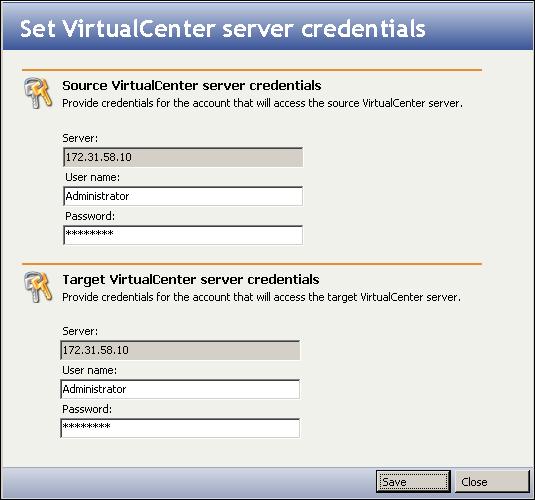
- If your source virtual machine is administered by VirtualCenter, select the VirtualCenter server in the Source VirtualCenter server field. The VirtualCenter server is where the VMware VirtualCenter service is running. The VMware VirtualCenter service manages all the VMware ESX servers in the environment. Selecting a VirtualCenter server provides the following benefits:
- Double-Take Availability for VMware Infrastructure will be able to accept a non-root user account.
- Double-Take Availability for VMware Infrastructure will be able to use VMotion technology to move the virtual machine.
To add additional VirtualCenter servers or to update credentials, see Managing VirtualCenter servers.
If you want to create a connection directly from one ESX server to another without using VirtualCenter, select (None).
- To browse virtual machines, either select a VirtualCenter server or enter the ESX host information, then click the Browse button to locate a virtual machine. The Select virtual machine window will appear.
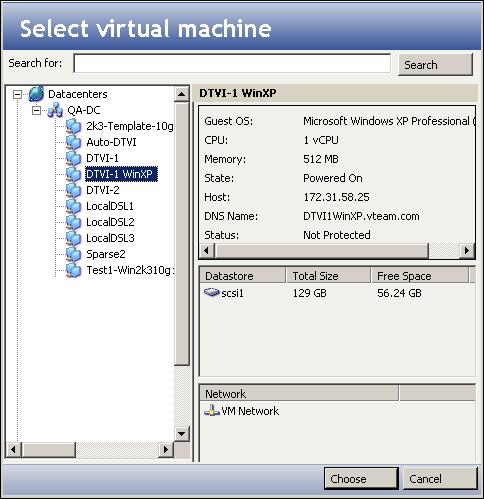
|
- In the Select virtual machine window, browse through the file tree on the left side to select a source virtual machine. When you select a virtual machine, the right pane is populated with information about the virtual machine, datastores, and networks associated with that virtual machine.
- To search for a virtual machine, enter all or part of the virtual machine name in the Search for field, then click Search. The virtual machines that meet the search criteria will appear in the Search Results folder in the left pane.
- After you have found the source virtual machine in the left pane, select it then click Choose.
- The Source ESX server IP address or DNS name field displays the IP address or DNS name of the selected VMware ESX server.
- In the User name field, enter the user name for the account you will be using to log on to the source VMWare ESX server.
- In the Password field, enter the password that is associated with the user account.
- After all fields have been completed, click Next. A window will display the progress as the Double-Take Availability for VMware Infrastructure console authenticates the source virtual machine.
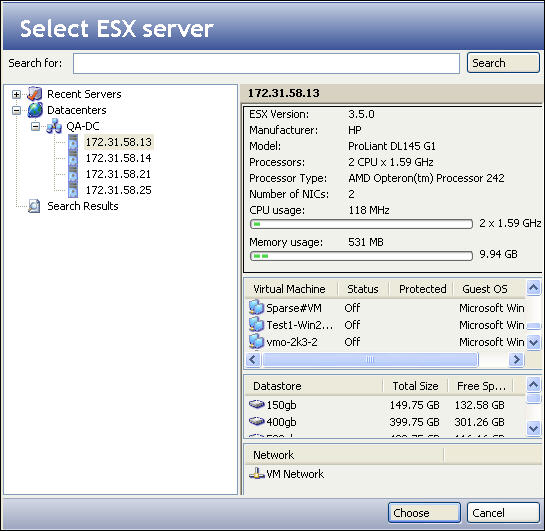
 Selecting the source virtual machine
Selecting the source virtual machine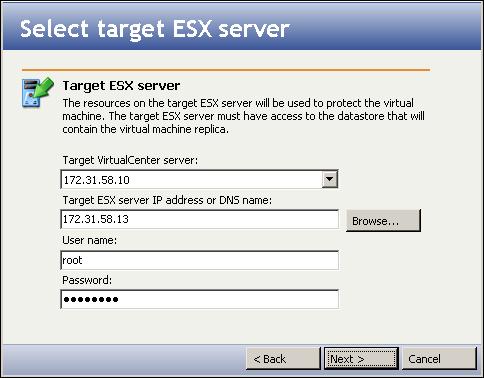
 Related Topics
Related Topics