Open topic with navigation
Selecting volumes to protect
If you have not done so already, launch the Double-Take Availability Virtual Recovery Assistant console.
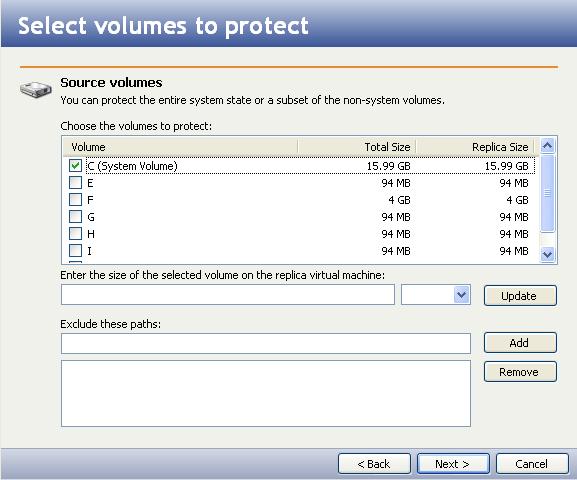
Select the volumes you want to protect to the target virtual machine. By default, the system volume will be selected.
|
Note:N
|
- Virtual Recovery Assistant can protect a maximum of 14 source volumes per SCSI controller installed on the Virtual Recovery Appliance virtual machine. Consult your VMware ESX documentation to determine how to install additional SCSI controllers on the Recovery Appliance.
- Virtual Recovery Assistant supports replication of junction points specific to domain controllers only. Any user-created junction points will be replicated as two unlinked copies of the data.
|
You can specify the size of the selected volume on the replica virtual machine.
- Select the name of the volume in the Volume table.
- Enter a value in the Size of the selected volume on the replica virtual machine field.
| Note: |
If the size of the virtual disk on the replica is identical to the size of the disk on the source and the source has less than 20 MB of disk space remaining, you may run out of disk space on the replica due to differences in how the virtual disk's block size is formatted. To avoid this issue, create a virtual disk with at least 20 MB more disk space than the amount of data that will be mirrored to it. |
- Use the drop-down box to select whether the value is in MB or GB.
- After you have entered information for the selected volume, click Update.
- Repeat this process to configure the size of additional volumes on the replica virtual machine.
- To exclude a path or folder from the protection, type the path to exclude in the Exclude these paths field, then click Add.
- To remove a path from being excluded, select the path, then click Remove.
- When you are finished selecting the data to protect, click Next.
Next step: Select target server