Open topic with navigation
Setting protection options
If you have not done so already, launch the Protect an entire server using a Hyper-V virtual machine workflow.
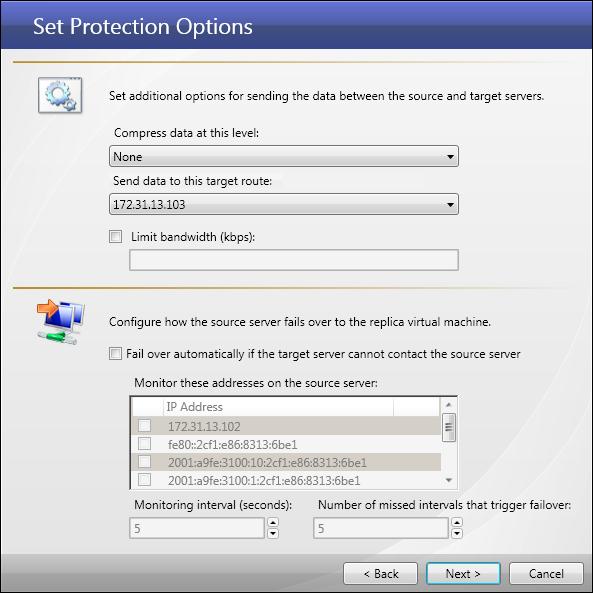
Configure the parameters for the protection job.
- Compression—Select the compression level (None, Low, Medium, or High) to use when sending data from the source to target server.
- Send data to this target route—Select the IP v4 or IP v6 address on the target server to which you want to send data from the source.
- Limit Bandwidth—You can specify a limit for the bandwidth to be used by source-to-target communications for this protection job. Select the Limit Bandwidth checkbox, then enter a value (in kilobits per second) that bandwidth cannot exceed.
- Fail over automatically if the target server cannot contact the source server—If you want the replica virtual machine to stand in for the source server when the source is inaccessible, select this checkbox.
|
Note:
|
Automatic failover will not occur until after the initial mirror has completed.
|
- Monitor these addresses on the source server—Select the IP address(es) to monitor for automatic failover.
- Monitoring interval (seconds)—(Default = 5) Select how often the monitor will check the source machine availability.
- Number of missed intervals that trigger failover—(Default = 5) Select how many monitor replies can be missed before assuming the source machine has failed.
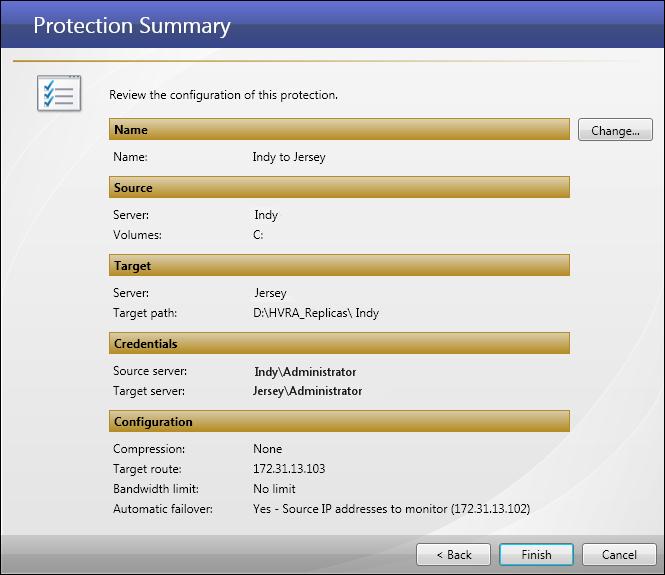
- When you have finished setting protection options, click Next. The Protection Summary window will appear.
- (Optional) If you want to change the name of the protection, click the Change button. The Change Name window will appear. Enter a new name for the protection, then click Save.
- Review the protection options, then click Finish to initiate the protection process.
After you click Finish, Double-Take Console creates the job. The Monitor Connections page will appear.
Next step: Monitor your protection job
 Related Topics
Related Topics