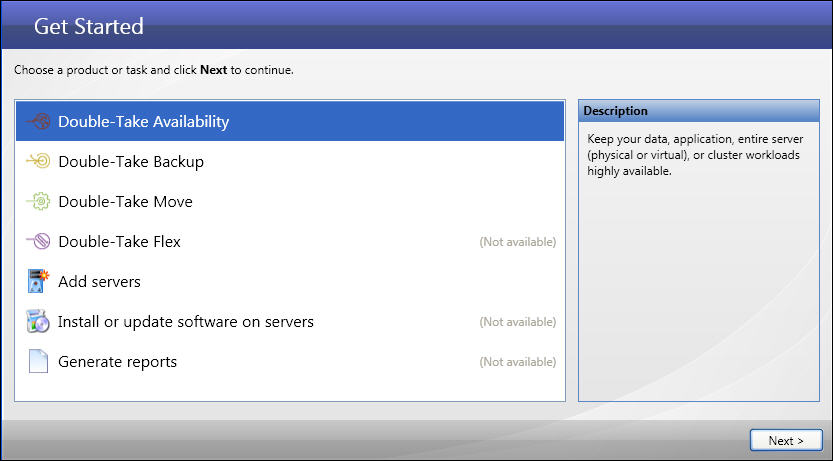
If you have not done so already, launch the Double-Take Console.

|
|
|
|
Note: |
Depending on which Double-Take components you have installed, you may see additional tasks on this screen. |
The workflow will guide you through the steps to configure protection for a physical source server whose data and system state you will be protecting with a virtual target server.
Next step: Select the source machine