If you have not done so already, launch the Protecting a SQL Server workflow.
The Connection tab includes options that will be applied to the specified source/target connection.
|
|
The following topics explain how to configure the options on the Connection tab:
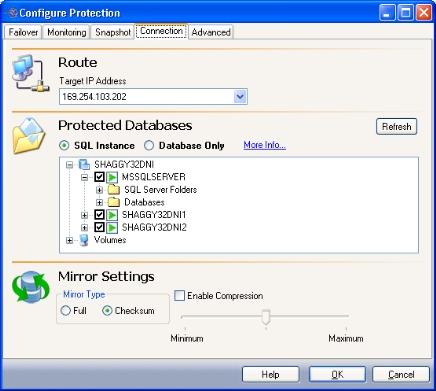
This setting identifies the Target IP Address that the Double-Take Availability data will be transmitted through. You should only change this setting if you want to select a different route for Double-Take Availability traffic. On a machine with more than one NIC, this increases the flexibility of configuring Double-Take Availability activity. For example, you can separate regular network traffic and Double-Take Availability traffic on a machine. The default ports will be used.
In a cluster, the route should be set to the name of the SQL dependent IP address.
For SQL, you can select one of the following protection modes:
Database only mode, many-to-one configurations
Select SQL Instance protection mode to replicate all of the SQL program and data files (except the \binn directory) to the target SQL server. This will allow the clients to access your production SQL Server data and functionality on the target in the event of a failure.
SQL Instance protection mode requires that the source and target servers both have the exact same version of SQL (major and minor versions) as well as similar logical drive structures (the target must have at least the same logical drives as the source where SQL program and data files are stored). Certain user databases can be de-selected, but the System databases (except for tempdb) are required.
You can also select non-application specific data under the Volumes folder.
|
Note: |
If Override Generated Rules is selected on the Advanced tab, this control will be disabled. |
To refresh the tree view to show new source directories or files that may have been added or removed, select the logical node, then click the Refresh button. If a node in the volumes branch is selected, then the items under that node will be refreshed.
The Database Only mode is intended for advanced users only.
Select Database Only protection mode to replicate only the .mdf, .ldf, and .ndf files to the target server. The selected database(s) will be attached to the target SQL Server upon failover, allowing clients to access the underlying data.
You can also select non-application specific data under the Volumes folder.
|
Note: |
If Override Generated Rules is selected on the Advanced tab, this control will be disabled. |
To refresh the tree view to show new source directories or files that may have been added or removed, select the logical node, then click the Refresh button. If a node in the volumes branch is selected, then the items under that node will be refreshed.
During the configuration and validation process, you will have the opportunity to transfer user logins and permissions (both server and database-level) and certain SQL Server registry and configuration settings to the target server. This will allow users to access the data associated with the selected database(s), but no other server-level functionality will be transferred to the target server (including but not limited to Job Server configuration, Full-Text service configuration, SQL Replication configuration, linked servers, remote servers, backup devices).
|
Note: |
|
|
If you select Database Only protection mode, you can select a non-system database and map it to a unique path on the target.
|
|
|
Note: |
The target database must be either offline or detached from the target before you can enable protection in the Application Manager. The validation test will detect if the target database is still online. Clicking Fix will detach that database on the target. |
|
Note: |
If Database-Only protection mode is used to protect SQL Server, attempting to attach a replicated SQL database on the target server after failover can fail when done outside of the Application Manager. The Double-Take service account (typically the target's LocalSystem account) is the account used to attach/detach databases on failover/failback. When the database is detached by the failback script, the Double-Take service account becomes the owner of those files that make up the database (*.mdf, *.ldf, etc.), and any attempts to manually attach the database may fail if the user account does not yet have NTFS permissions to access the physical files. To change the permissions on an individual file, perform these steps on each file that is part of the database's file list.
|
The following examples describe the SQL many-to-one configurations that can be protected using Application Manager.
Example 1: If you have two SQL servers (Source1 and Source2) where each server has only the default instance installed, you can protect databases from both servers' default instance, provided that the database names are unique.
Case 1: Both source servers’ default instances have a database named “Accounting”. You can only protect/failover one server's copy of the database (because SQL on the target will not allow you to attach more than one copy of the same-named database).
|
Note: |
If you select and setup both servers’ default instances for protection and both source servers fail, the “Accounting” database on the first source server to be failed over will be attached. The second server to failover will not be able to attach its “Accounting” database. |
Case 2: If Source1 has a database named “Accounting1”, and Source2 has a database named “Accounting2”, then you can protect and failover the database on both servers without any issues.
|
Note: |
All database filenames (*.mdf, *.ldf, and *.ndf) must either be:
|
Example 2: If you have two SQL servers (Source3 and Source4) where each has a named instance installed (for example, Source3\instance1 and Source4\instance2), you can protect databases from both servers if the target has at least those two instances installed (Target1\instance1 and Target1\instance2).
Case: Both source SQL servers have a database named “Accounting” (Source3\instance1|Accounting and Source4\instance2|Accounting). You can protect and failover each SQL server’s copy of the database without any issue.
|
Note: |
All the database filenames (*.mdf, *.ldf, and *.ndf) must either be:
|
The following options specify what files you want sent from the source to the target during a mirror.
|
Note: |
The Mirror type setting also applies to the restoration connection. |
This setting enables compression of data that is transmitted from the source to the target. Significant improvements in bandwidth utilization have been seen in Wide Area Network (WAN) configurations or in any case where network bandwidth is a constraint.
Compression may be used in Local Area Network (LAN) configurations, though it may not provide any significant network improvements.
You can specify compression for different source/target connections, but all connections to the same target will have the same compression settings.
By default, compression is disabled. To enable it, select Enable Compression, then set the level from minimum to maximum compression.
Next step: Configure advanced settings
 Route
Route