

|
Use these instructions for physical to ESX protection.
Specify the
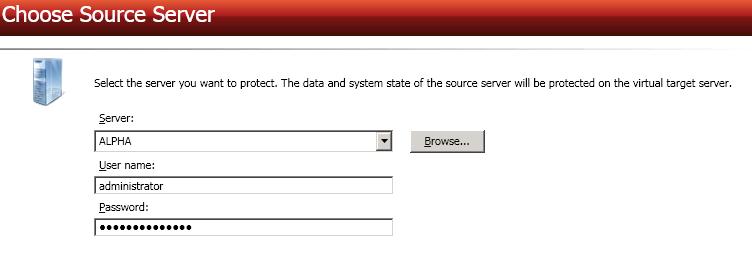
Server—Specify the name or IP address of the physical server that you want to protect. You can click Browse to select a server from a network drill-down list.
If you enter the source server's fully-qualified domain name, the Double-Take Console will resolve the entry to the server short name. If that short name resides in two different domains, this could result in name resolution issues. In this case, enter the IP address of the server.
Your source can have no more than ten NICs enabled.
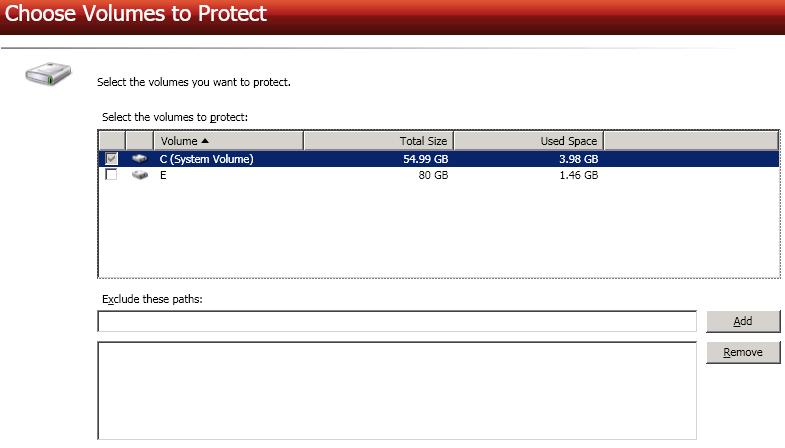
Choose the volumes on the source server that you want to protect.
Specify the target server.

Server—Specify the name or IP address of the target server. You can click Browse to select a server from a network drill-down list.
If you enter the target server's fully-qualified domain name, the Double-Take Console will resolve the entry to the server short name. If that short name resides in two different domains, this could result in name resolution issues. In this case, enter the IP address of the server.
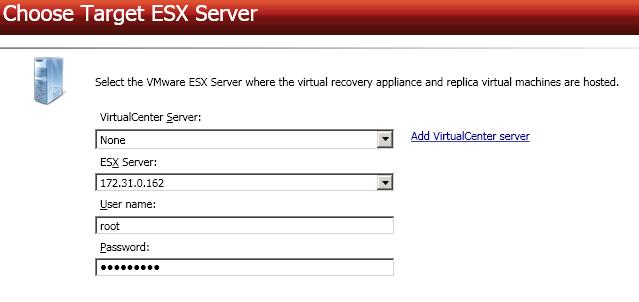
Specify the ESX server information for your target virtual recovery appliance.
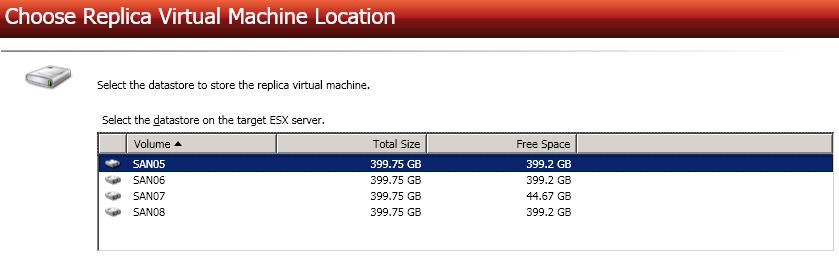
Select one of the volumes from the list to indicate the default datastore on the target where you want to store the new virtual server when it is created. The target volume must have enough Free Space to store the source data. You will be able to make additional datastore selections before enabling your protection.
Configure the replica virtual machine that will be created on the target.
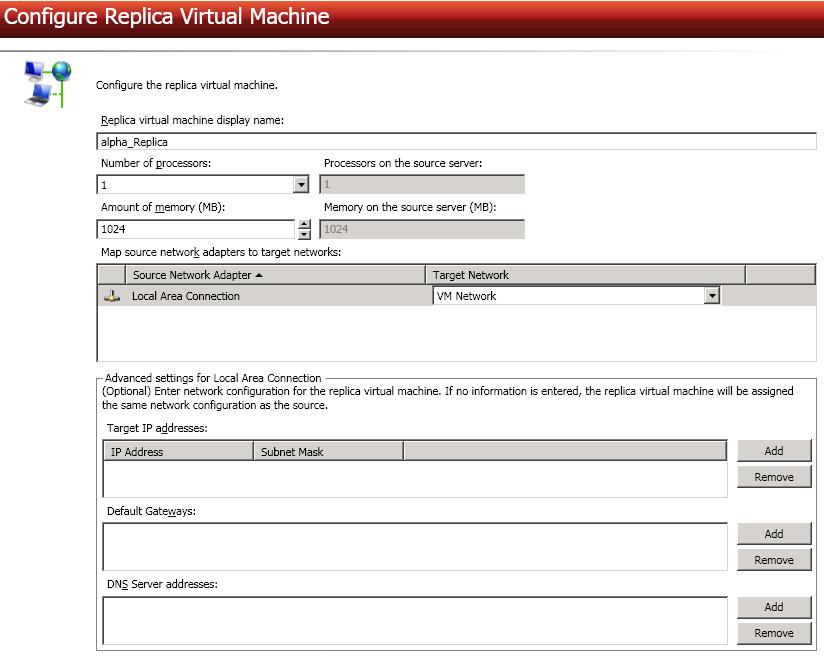
Advanced settings—These fields will allow you to configure advanced settings, which are used primarily for WAN support. For each Source Network Adapter, you can specify Target IP addresses, Default Gateways, and DNS Server addresses.
Updates made during failover will be based on the network adapter name when protection is established. If you change that name, you will need to delete the job and re-create it so the new name will be used during failover.
If you update one of the advanced settings (IP address, gateway, or DNS server), then you must update all of them. Otherwise, the remaining items will be left blank. If you do not specify any of the advanced settings, the replica virtual machine will be assigned the same network configuration as the source.
Configure the volumes on the replica virtual machine that will be created on the target.
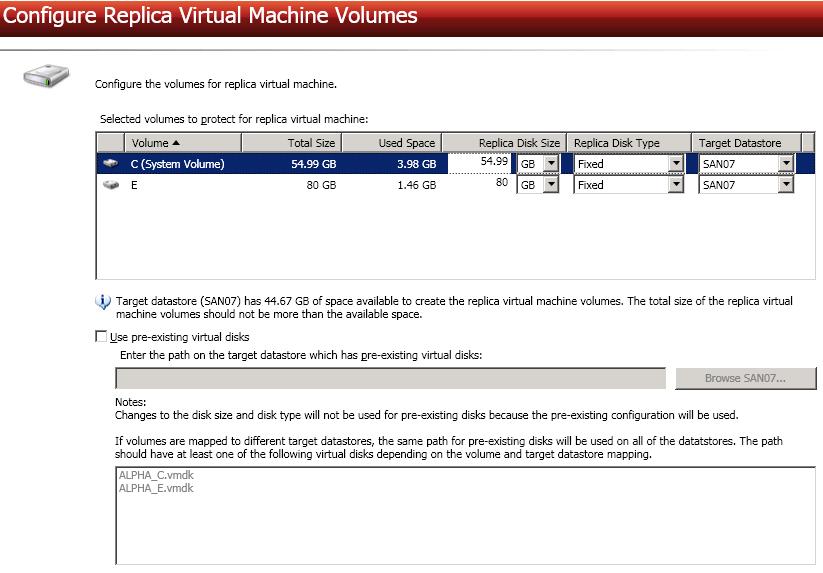
Replica Disk Size—For each volume you are protecting, specify the size of the replica virtual machine on the target. Be sure and include the value in MB or GB for the disk. The value must be at least the size of the specified Used Space on that volume. You will be unable to edit the disk size for a volume if you select Use pre-existing virtual disks, because the pre-existing configuration will be used.
In some cases, the replica virtual machine may use more virtual disk space than the source volume due to differences in how the virtual disk's block size is formatted and how hard links are handled. To avoid this issue, specify the size of your replica to be at least 20 MB larger.
Use pre-existing virtual disks—
Because Double-Take Availability will skip the virtual disk creation steps when using a pre-existing disk, Double-Take Availability will instead copy your existing virtual disk to the default VMware new virtual machine location. Therefore, it is important that you do not place your existing virtual disk in the new folder location that VMware will create. Put the pre-existing virtual disk in a temporary location on the target. Specify this temporary location for Enter the path on the target data store which has pre-existing virtual disks.
In order for Double-Take Availability to find the pre-existing disk, the virtual disk file names must be formatted using the convention SourceServer_DriveLetter. For example, if your source server is Alpha and you are protecting drives C and D, Double-Take Availability will look for the file names Alpha_C.vmdk and Alpha_D.vmdk. If you are using IP addresses, substitute the IP address for the server name. For example, if the IP address for server Alpha is 172.31.10.25 then Double-Take Availability will look for the file names 172.31.10.25_C.vmdk and 172.31.10.25_D.vmdk.
If you originally created a virtual disk and specified the source server by its IP address, the pre-existing virtual disk file name cannot use the server name. However, you can rename that file and its associated -flat.vmdk file to use the IP address. The reverse is also true. If you originally specified the source server by its name, the pre-existing virtual disk file name cannot use the server’s IP address. However, you can rename the file and its associated -flat.vmdk to use the source name. For example, if you originally created a virtual disk and specified the source by its IP address, you need to rename the file source_name_drive.vmdk to source_IPaddress_drive.vmdk. You also need to rename the file source_name_drive-flat.vmdk to source_IPaddress_drive-flat.vmdk. The reverse (change source_IPaddress to source_name for both files) is also true. Additionally, you will need to edit the .vmdk file manually because it contains the name of the -flat.vmdk file. Modify the reference to the -flat.vmdk file to the new name you have specified using any standard text editor.
In a WAN environment, you may want to take advantage of the Use pre-existing virtual disks feature by using a process similar to the following.
Specify your protection settings.
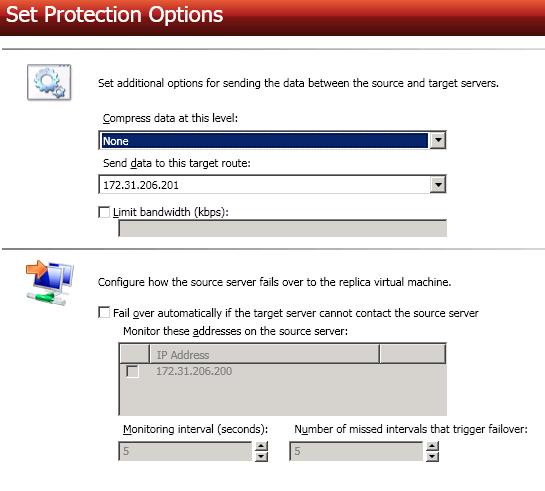
Number of missed intervals that trigger failover—If you have enabled automatic failover, specify the number of monitor replies sent from the source to the target that can be missed before assuming the source has failed.
To achieve shorter delays before failover, use lower interval and missed interval values. This may be necessary for servers, such as a web server or order processing database, which must remain available and responsive at all times. Lower values should be used where redundant interfaces and high-speed, reliable network links are available to prevent the false detection of failure. If the hardware does not support reliable communications, lower values can lead to premature failover. To achieve longer delays before failover, choose higher values. This may be necessary for servers on slower networks or on a server that is not transaction critical. For example, failover would not be necessary in the case of a server restart.
If you need to modify a job's settings after it has been created, you can do so after the mirror has completed by highlighting the job on the Manage Jobs page, selecting View Job Details, and then clicking the View job properties link. You will be taken back to the Protection Summary page where you can edit the job's settings..