

|
Select the virtual machine that you want to protect.
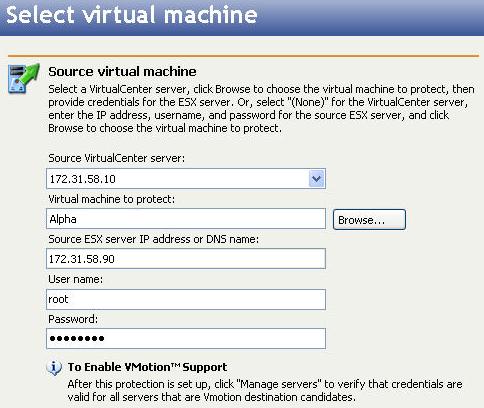
Virtual machine to protect—Specify the name of the virtual server you want to protect. You can click Browse to select a server from a network drill-down list or to search for a server. Once you have specified a virtual server to protect, the IP address or DNS of the ESX server will be displayed.
Each protection job applies to a single virtual machine.
Virtual machines using ESX raw or independent disks are not supported.
If your virtual machine is configured to use thin (sparse disks), the replica on the target will not be a thin disk. Make sure there is adequate space on the target.
The virtual machine name cannot contain any of the following special characters.
# / \ : * ? ' " < > |
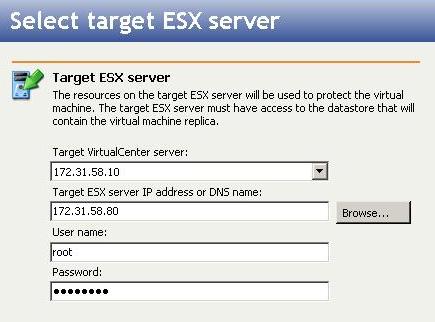
Specify the target ESX server that will store the replica virtual machine.
Select a datastore on the target where the source virtual machine data will be replicated.
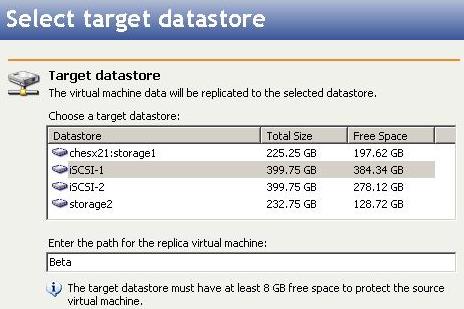
Enter the path for the replica virtual machine—Specify a location to store the replica of the source virtual machine. By default, the location will be named the source virtual machine name.
The replica virtual path cannot contain any of the following special characters.
# / \ : * ? ' " < > |
By specifying a datastore and path with an existing virtual disk, you can reuse an existing virtual machine created by a previous protection job. This can be useful for pre-staging data on a virtual machine over a LAN connection and then relocating it to a remote site after the initial mirror is complete. When you reuse a virtual machine, Double-Take Availability for VMware Infrastructure performs a difference mirror which saves times. Use the following steps to reuse a virtual machine.
Configure the replica virtual machine.
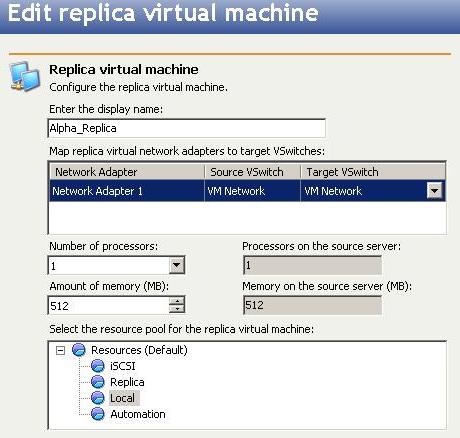
Enter the display name—Specify the name for the replica virtual machine. The name cannot contain any of the following special characters.
# / \ : * ? " " < > |
When you are satisfied with your workflow selections, click Finish, and you will automatically be taken to the Monitor protection page.
The target virtual machine is registered when replication is started and will remain registered. To unregister a machine, you must click Delete Protection and choose Delete the associated replica virtual machine.
Even though the target virtual machine appears to be available on the ESX server, it should not be powered on, removed, or modified while it is owned by an active protection job, otherwise the target virtual machine will become corrupt and break the protection job.
Do not attempt to manually create or delete snapshots on the protected virtual machine. This will disrupt the protection of the virtual machine and may generate unpredictable results on the source and target virtual machines.
Double-Take Availability for VMware Infrastructure supports generic SCSI device mappings in virtual machines, however, the generic SCSCI device will not be created on the target virtual machine during failover because the target virtual machine will fail to start if the SCSI device hardware does not exist on the target ESX host. After failback, the generic SCSI device will be mapped back to the original source, but the SCSI device will not be mapped back to the original source if the protection job is re-created in the reverse direction.