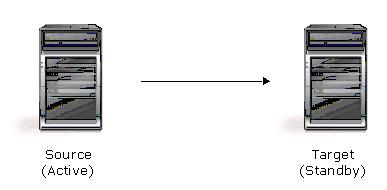
| Description | One target server, having no production activity, is dedicated to support one source server. The source is the only server actively replicating data. |
| Applications |
|
| Considerations |
|
Double-Take Availability is an exceptionally flexible product that can be used in a wide variety of network configurations. To implement Double-Take Availability effectively, it is important to understand the possible configuration options and their relative benefits. Double-Take Availability configuration options can be used independently or in varying combinations.

| Description | One target server, having no production activity, is dedicated to support one source server. The source is the only server actively replicating data. |
| Applications |
|
| Considerations |
|
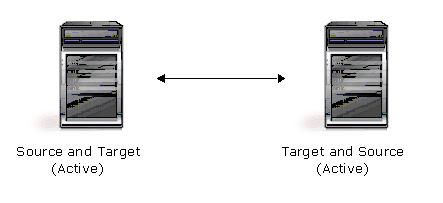
| Description | Each server acts as both a source and target actively replicating data to each other |
| Applications | This configuration is appropriate for failover and critical data backup. This configuration is more cost-effective than the Active/Standby configuration because there is no need to buy a dedicated target server for each source. In this case, both servers can do full-time production work. |
| Considerations |
|
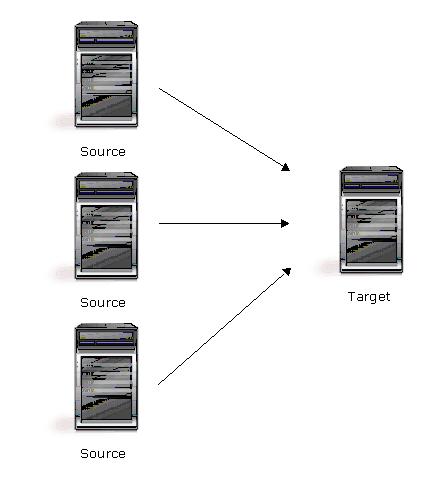
| Description | Many source servers are protected by one target server. |
| Applications | This configuration is appropriate for offsite disaster recovery. This is also an excellent choice for providing centralized tape backup because it spreads the cost of one target server among many source servers. |
| Considerations |
|
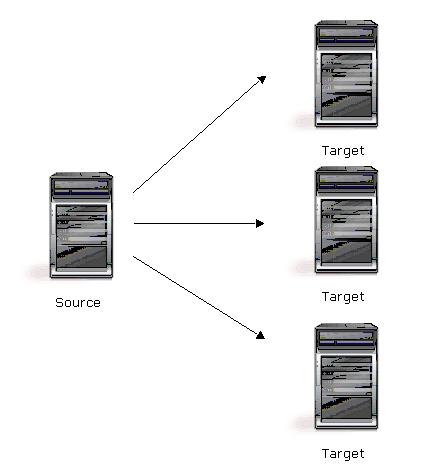
| Description | One source server sends data to multiple target servers. The target servers may or may not be accessible by one another. |
| Applications | This configuration provides offsite disaster recovery, redundant backups, and data distribution. For example, this configuration can replicate all data to a local target server and separately replicate a subset of the mission-critical data to an offsite disaster recovery server. |
| Considerations |
|
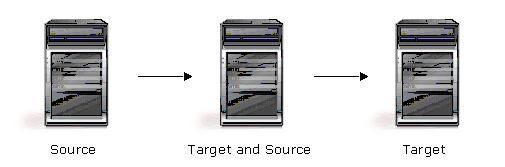
| Description | The source servers sends replicated data to a target server, which acts as a source server and sends data to a final target server, which is often offsite. |
| Applications | This is a convenient approach for integrating local high availability with offsite disaster recovery. This configuration moves the processing burden of WAN communications from the source server to the target/source server. After failover in a one-to-one, many-to-one, or one-to-many configuration, the data on the target is no longer protected. This configuration allows failover from the first source to the middle machine, with the third machine still protecting the data. |
| Considerations |
|
 One-to-one, active/standby
One-to-one, active/standby Related Topics
Related Topics