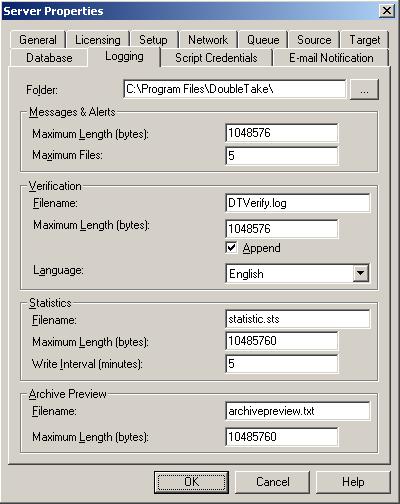
A verification log is created on the source during the verification process. The log identifies what is verified as well as which files are not synchronized.

| Note: | Changes made to the verification log in the Server Properties, Logging tab will apply to all connections from the current source machine. |
In the log file, each verification process is delineated by beginning and end markers. A list of files that are different on the source and target is provided as well cumulative totals for the verification process. The information provided for each file is the state of its synchronization between the source and the target at the time the file is verified. If the remirror option is selected so that files that are different are remirrored, the data in the verify log reflects the state of the file before it is remirrored, and does not report the state of the file after it is remirrored. If a file is reported as different, review the output for the file to determine what is different.
The mask must be converted in order to determine what attributes are assigned to a file. The mask is a hexadecimal number corresponding to a binary number that indicates what the attributes are. Using the following steps, you can determine how the mask corresponds to the attributes of a file.
| Position (from right to left) | Attribute | Sample Hexadecimal Number 23 |
|---|---|---|
| 1 | Read only | 1 |
| 2 | Hidden | 1 |
| 3 | None | 0 |
| 4 | System | 0 |
| 5 | Directory | 0 |
| 6 | Archive | 1 |
| 7 | Encrypted | 0 |
| 8 | Normal | 0 |
| 9 | Temporary | 0 |
| 10 | Sparse file | 0 |
| 11 | Reparse point | 0 |
| 12 | Compressed | 0 |
|
13 |
Offline | 0 |
| 14 | Not content indexed | 0 |
| 15 | None | 0 |
| 16 | None | 0 |
| Note: | Files that were replicated with the Replicate NT Security by Name feature enabled, will be identified as different in the log file because of the local name attribute. The files will be the same. |